24/7 Security Monitoring and Response
Real-time protection of your laptops, servers, cloud and IT environment against cyber threats.

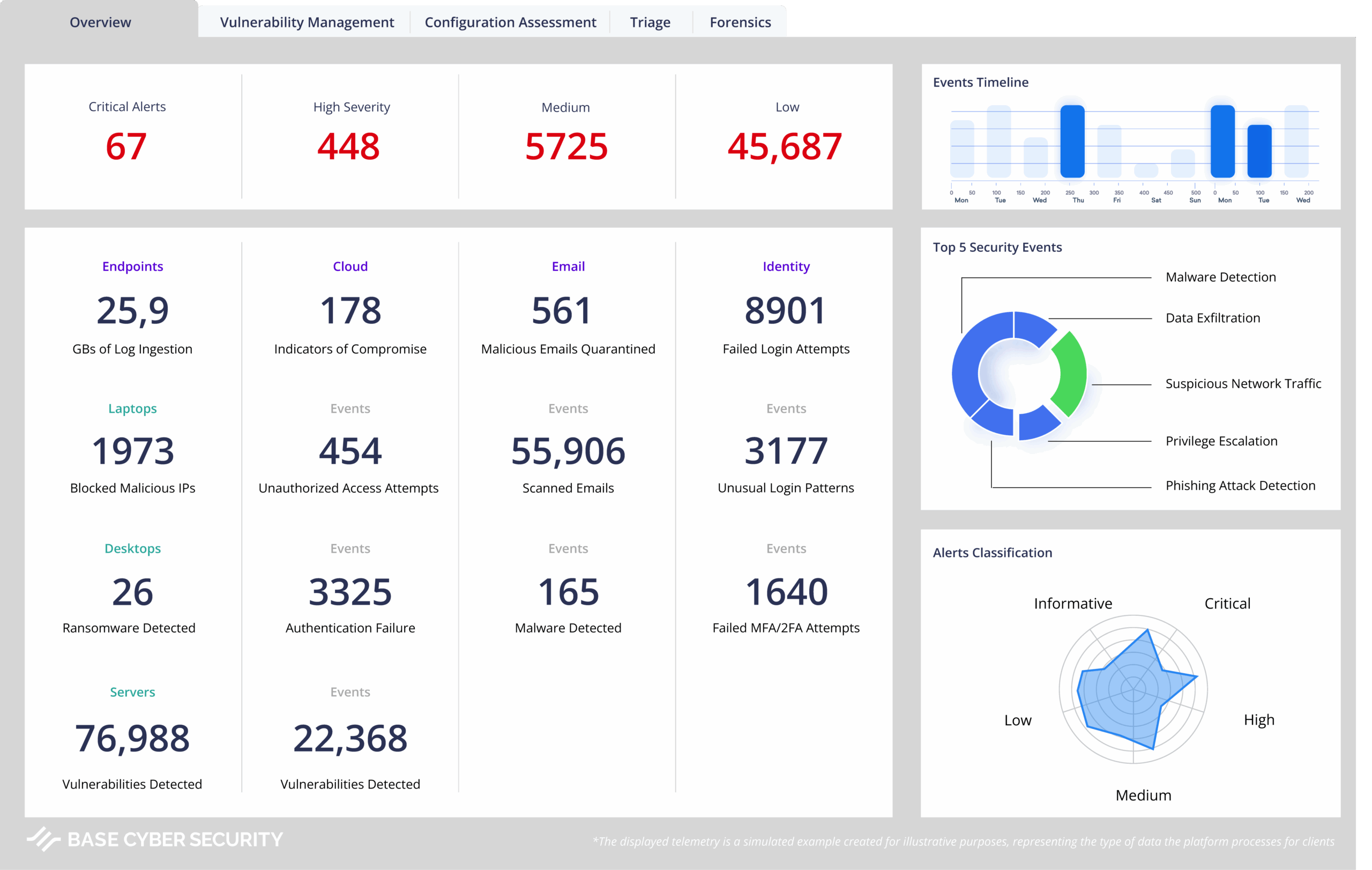
Better coverage equals better protection
Connect your environment to our Security Operations Center (SOC) for advanced coverage and protection
Outsource all your security and privacy governance, risk and compliance documentation, from Data Protection Agreement’s (DPA) to answering Security Assessments Questionnaires and everything in between.
Receive your monthly security insights report.
Your security report provides an in-depth view of detected threats, actions taken, and emerging trends in your organization’s cybersecurity. It enables you to prioritize security efforts by highlighting high-risk areas and offering specific recommendations. This actionable insight helps your team strengthen defenses and address vulnerabilities proactively.
Level up your security, and drive business growth
Your organization isn’t truly secure just because a pentest was completed, 24/7 security monitoring is in place, or compliance with an industry standard has been achieved. True security comes from doing what makes sense for your business—built on an integrated approach that builds trust with your customers and protects your organization while driving business growth. Our penetration testing and vulnerability assessment services are designed to help you make smart, business-driven security decisions.

Simple steps to real-time protection
Getting protected is fast and hassle-free. Simply connect your IT environment to our Security Operations Center, and within minutes you’ll have continuous monitoring, active threat detection, and rapid response in place
Step 1: Discovery
In a first conversation we discuss your monitoring and response needs, decide on a best way forward.
Step 1: Endpoint Inventory and Selection
Together we decide which endpoints have company data and need to be monitored. We also develop an playbook approach to security incidents, keeping track of who to contact within the organization.
Step 2: Deploy Agents
Connect us with your IT person and we’ll connect your endpoints in a moment’s notice
Step 3: Verification
Verification and check to see if all endpoints are connected and telemetry is being received in our Security Operations Center
Step 4: Analysis
We gather and analyze your data in real-time. In case our SOC finds urgent matters that require your immediate attention, they will contact you directly.
Step 5: Your first Report
We share findings with you periodically in an actionable report and are discuss the findings with you.
Upgrade Your Cybersecurity With a Monthly Subscription
Our Incident Response retainer is a monthly subscription that gives your organization priority access to a dedicated team of experts—ready to respond immediately in the event of a cyberattack. This proactive arrangement ensures faster containment, reduces downtime, and limits the overall impact of security incidents.
Sign up for Incident Response
Level up your security, and drive business growth
Your organization isn’t truly secure just because a pentest was completed, 24/7 security monitoring is in place, or compliance with an industry standard has been achieved. True security comes from doing what makes sense for your business—built on an integrated approach that builds trust with your customers and protects your organization while driving business growth.
Frequently Asked Questions
That’s any device used that may contain data about your company.
Security Monitoring is charged per device, so any laptop, cloud environment or otherwise is charged at a specific rate per month.
Ultricies ligula sed magna dictum porta. Mauris blandit aliquet elit, eget tincidunt nibh pulvinar a.
Vestibulum ante ipsum primis in faucibus orci luctus et ultrices posuere cubilia Curae; Donec velit neque, auctor sit amet aliquam vel, ullamcorper sit amet ligula.
Nulla quis lorem ut libero malesuada feugiat. Donec rutrum congue leo eget malesuada.
Nulla porttitor accumsan tincidunt. Vestibulum ante ipsum primis in faucibus orci luctus et ultrices posuere cubilia Curae; Donec velit neque, auctor sit amet aliquam vel, ullamcorper sit amet ligula.
Talk to



