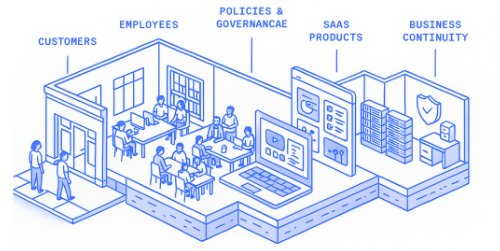
We help you select, implement and maintain the right security controls for your scale up and level of risk.
You are now a scale-up focused on rapid growth in revenue, customers, and market presence. This is the stage where you expand operations, grow your teams, and broaden your product offerings to capture a bigger share of the market.
Security needs to match the risk level of your business — protect your company, earn customer trust, and help you grow. We provide end-to-end protection for your entire organization. From protecting your laptops and servers to other devices and cloud environments, our solutions keep your business secure, compliant, and resilient.
Our approach ensures consistent protection, compliance with industry standards, and resilience against evolving cyber threatsWe protect your entire organization —build resilience, protect business continuity, and build customer trust
Over 50+ companies globally have trusted us to level up the security of their organization.
Strong organizational security isn’t just about defense. It’s about trust.
Clients, partners, and regulators expect your business to protect sensitive data and ensure seamless service continuity. Modern security spans every layer of your organization—from safeguarding networks, devices, and cloud environments to training employees and staying compliant with ever-evolving regulations. Investing in comprehensive organizational security is no longer optional—it’s essential. It builds trust, strengthens resilience, and empowers your business to grow, innovate, and stay competitive in a rapidly changing world.
We take your organization’s security to the next level — from penetration testing and 24/7 monitoring to compliance and security awareness training. We help make your business resilient in the face of cyber risk.
Nobody starts a company to struggle with IT Security. Whether you need to build secure digital products for your clients, want to protect your company against cyber threats, or have to complete security assessments – at some point security will play an important role.
Level up your security, and drive business growth
Your organization isn’t necessarily secure because you’ve completed a pentest, implemented 24/7 monitoring, or met compliance requirements. Real security comes from doing what makes sense for your business — through an integrated approach that protects your operations, builds customer trust, and supports sustainable growth.
That’s why our security services are designed to help you make informed, business-driven security decisions. We focus on identifying what matters most, prioritizing quick wins, and creating a clear plan to address deeper issues over time — all with your business goals in mind.
Frequently Asked Questions
That’s any device used that may contain data about your company.
Security Monitoring is charged per device, so any laptop, cloud environment or otherwise is charged at a specific rate per month.
Ultricies ligula sed magna dictum porta. Mauris blandit aliquet elit, eget tincidunt nibh pulvinar a.
Vestibulum ante ipsum primis in faucibus orci luctus et ultrices posuere cubilia Curae; Donec velit neque, auctor sit amet aliquam vel, ullamcorper sit amet ligula.
Nulla quis lorem ut libero malesuada feugiat. Donec rutrum congue leo eget malesuada.
Nulla porttitor accumsan tincidunt. Vestibulum ante ipsum primis in faucibus orci luctus et ultrices posuere cubilia Curae; Donec velit neque, auctor sit amet aliquam vel, ullamcorper sit amet ligula.
Talk to